An Agency's Guide to Surviving the Data Breach Era
Updated on
Published on

The advertising industry is facing a critical inflection point, where digital creativity and data-driven strategy are shadowed by persistent cybersecurity threats. The recent, high-profile data breach at Dentsu's subsidiary, Merkle, serves as a stark warning, not an anomaly. This incident, which exposed sensitive employee and client data, underscores a new reality: an agency data breach is no longer a distant possibility but an imminent business risk. The assets at stake are an agency's lifeblood: confidential client lists, proprietary campaign strategies, financial records, and the invaluable currency of brand reputation. A single security failure can dismantle years of trust and inflict catastrophic financial damage. This guide deconstructs the primary threats confronting modern agencies and provides an actionable playbook for building a resilient defense, ensuring compliance, and protecting the trust that underpins every client relationship.

Deconstructing the Modern Threat Landscape for Agencies
To build an effective defense, agencies must first understand the specific nature of the attacks targeting them. The modern threat landscape is multifaceted, blending technical exploits with sophisticated psychological manipulation. Attackers are highly motivated, often seeking financial gain or access to the high-value data agencies manage for their clients. Acknowledging these specific vectors is the first step toward mitigating them.
The Human Element: Phishing and Social Engineering
Despite advanced security technologies, the most vulnerable point in any agency’s defense remains its people. Employees, particularly those in client-facing or financial roles like account managers and finance personnel, are prime targets for sophisticated phishing and social engineering attacks. These attacks use deceptive emails, disguised as legitimate communications, to trick staff into revealing credentials, executing malicious attachments, or authorizing fraudulent payments. A stark example is the data breach at Roger Keith & Sons Insurance Agency, which began with a successful phishing attack and ultimately compromised a vast amount of sensitive personal and financial data. This incident demonstrates how a single human error can trigger devastating consequences. Furthermore, these attacks are often precursors to larger incidents; ransomware, frequently initiated through phishing, now accounts for 5% of all data breaches, highlighting the severe financial motives behind targeting employees.
Vulnerabilities in the Digital Supply Chain
Modern agencies operate within a complex ecosystem of third-party vendors, SaaS platforms, and specialized martech tools. While these partnerships are essential for delivering cutting-edge services, they also introduce significant security risks. An agency’s defense is only as strong as its weakest link, and a vulnerability in any part of its digital supply chain can be exploited. The data leak at Reputation.com serves as a powerful case study; a vulnerability in the online reputation management firm's system exposed 120 million records, potentially compromising the social media accounts of the major brands they serve. This incident shows that even without a direct attack on an agency's own network, its client data can be put at risk, making rigorous vendor security vetting a critical and non-negotiable process.
Ransomware and Data Exfiltration
Ransomware attacks have become a dual-threat crisis for businesses. Attackers are no longer content with simply encrypting an agency's files and disrupting operations. In a tactic known as double extortion, they first exfiltrate, or steal, large volumes of sensitive data before deploying the ransomware. They then threaten to leak this stolen information publicly if the ransom is not paid, adding immense pressure on the victim organization. The Dentsu breach exemplifies this modern attack method, where threat actors stole files containing employee bank details, salary information, and client data before the incident was fully contained. This strategic shift from business disruption to a full-blown data crisis makes ransomware an existential threat, capable of causing severe financial, legal, and reputational damage simultaneously.
Building a Resilient Cybersecurity Framework
Reacting to threats is insufficient; agencies must build a proactive and multi-layered cybersecurity framework to survive the data breach era. This involves establishing foundational controls, securing the flow of high-value digital assets, and extending security diligence to all external partners. A resilient framework is not a one-time project but a continuous program of assessment, improvement, and vigilance that becomes part of the agency's operational DNA.
Foundational Security Measures
A proactive defense is built upon a set of non-negotiable security controls that reduce the attack surface and mitigate the most common threats. Implementing these foundational measures is the most effective way to elevate an agency's security posture from reactive to resilient. These practices should be enforced universally across the organization, forming the baseline for all security efforts.
- Multi-Factor Authentication (MFA): Implement MFA across all critical systems, including email, VPN, cloud platforms, and financial software. This provides a crucial second layer of defense against unauthorized access resulting from compromised credentials.
- Regular Security Awareness Training: Conduct ongoing, engaging training programs to educate all employees on how to identify phishing attempts, practice good password hygiene, and handle sensitive data responsibly. A well-informed team is the best human firewall.
- The Principle of Least Privilege: Ensure employees only have access to the specific data and systems absolutely necessary to perform their job functions. This limits the potential impact of a compromised account by preventing lateral movement by an attacker.
- Consistent Patch Management: Establish a rigorous and timely process for applying security patches to all software, servers, and devices. Unpatched vulnerabilities are one of the most common entry points for attackers.
- Comprehensive Incident Response Plan: Develop, document, and regularly test a detailed plan that outlines the exact steps to take in the event of a security incident, from detection and containment to communication and recovery.
Securing High-Value Digital Assets
Agencies are custodians of highly sensitive information, from client contracts and campaign briefs containing Personally Identifiable Information (PII) to the strategic documents that define a massive campaign like Walmart's marketing strategy. Standard communication tools like email are often insufficient for transferring this data and pose a significant risk. Traditional methods for transferring sensitive documents are inherently insecure and can expose agencies and their clients to unnecessary risk.
To meet today’s security and compliance expectations, agencies should use secure communication protocols for transmitting sensitive documents. One option is a compliant online fax service; for example, iFax offers encrypted document transmission and supports compliance needs for organizations that handle regulated information. With web, desktop, and mobile access, tools like this can let teams send and receive documents from anywhere while reducing the risks associated with traditional fax machines or unencrypted email, helping strengthen an agency’s overall data-protection framework.
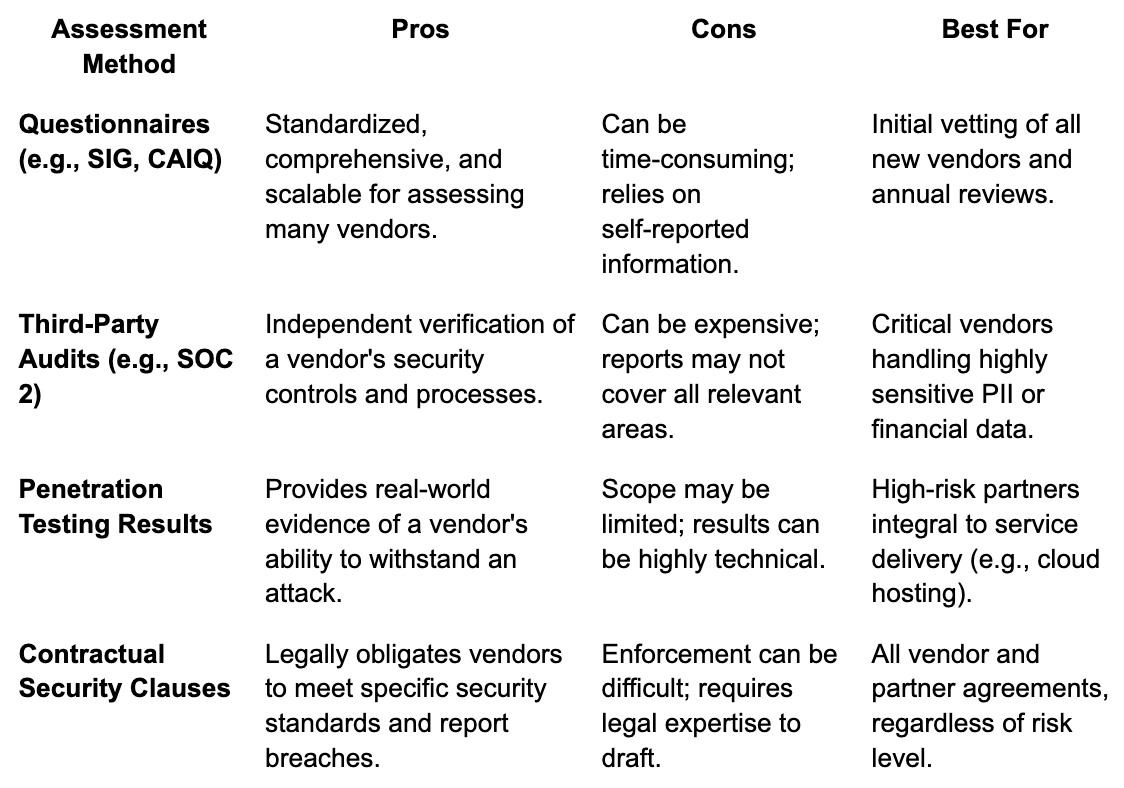
Vendor and Partner Risk Management
Performing thorough due diligence on all third-party vendors is no longer optional. An agency is ultimately responsible for protecting client data, even when it is being handled by a martech platform or a freelance partner. A structured approach to vendor risk management is essential for identifying and mitigating potential security gaps in the digital supply chain. Different methods of assessment are appropriate for vendors of varying risk levels.
Incident Response and Crisis Management
Even with the strongest defenses, a breach is always possible. How an agency responds in the moments, hours, and days following an incident is what separates a manageable event from a catastrophic failure. An effective incident response is not improvised; it is a well-rehearsed plan executed with speed, precision, and transparency to minimize damage and preserve client trust.

The First 48 Hours: Detection and Containment
Speed and decisiveness are paramount in the initial hours of a breach. The primary goal is to stop the attack and prevent further damage. Upon detecting suspicious activity, the incident response plan must be activated immediately. This involves assembling the designated response team, isolating affected systems from the network to prevent the threat from spreading, and preserving evidence for forensic analysis. As seen in the Dentsu incident, a critical best practice is to engage external experts swiftly. The company reported that it immediately initiated its incident response protocols and brought in a specialist cybersecurity firm to investigate the scope of the attack. This third-party validation is crucial for an accurate assessment and a credible response.
Communication and Transparency
Managing communications during a crisis is as important as the technical response. A clear, honest, and timely communication strategy is essential for maintaining trust with clients, employees, and regulators. The plan must outline who needs to be notified, when, and with what information, ensuring compliance with all applicable data breach notification laws. A poorly handled response can amplify the damage, both financially and reputationally. The average cost of a data breach for a small business can range from $120,000 to $1.24 million, a figure that is often compounded by the loss of clients and the immense cost of rebuilding a tarnished brand reputation. Protecting that reputation, as demonstrated by the enduring power of the Coca-Cola marketing strategy, is a primary business objective that transparent crisis communication helps to secure.
Post-Breach Analysis and Fortification
The work is not finished once an incident is contained and stakeholders have been notified. A thorough post-mortem analysis is essential to understand the root cause of the breach and prevent a recurrence. This process should identify the specific vulnerabilities that were exploited, whether they were technical, procedural, or human-related. The findings from this analysis must then be used to strengthen security controls, update policies, and refine the incident response plan with lessons learned. This continuous feedback loop transforms a negative event into a catalyst for building a more mature and resilient defense for the future.
Navigating the Future of Agency Data Security
Surviving the data breach era requires a fundamental shift in mindset for advertising agencies. The key pillars of a resilient posture are clear: a deep and current understanding of the threat landscape, the implementation of a multi-layered defense that includes secure file transfer and communication channels, and a well-rehearsed incident response plan. Cybersecurity can no longer be viewed as a peripheral IT function or a compliance checkbox; it is a central pillar of an agency's value proposition and a core component of client service. In an industry defined by data, the ability to protect client information is the ultimate measure of trust, reliability, and professional responsibility. For agencies dedicated to safeguarding their most valuable assets—their clients' data and their own reputation—adopting a proactive and comprehensive security posture is the only definitive path to long-term resilience and success.









